Access control in ArangoDB Oasis
Oasis has a level structured set of resources that are subject to access control:
- Organizations
- Projects
- Deployments
Each of these resources have a set of operations that can be invoked upon them. For example, you can create a project in an organization. This requires the respective permission, which can be granted to organization members via a role such as the pre-defined Project Administrator.
The association of a member with a role is called a role binding. All role bindings of a resource combined form the so called policy.
Roles can be bound on organization, project and deployment level. The lower levels inherit permissions from their parent resources.
Policy
To give a user (or a group of users) access to resources of Oasis, you assign a role to that user (or group). This is done in a policy.
A policy is the set of a bindings of roles to users (or groups) for a specific resource. This means that there is a unique policy per resource.
For example, the Oasis Introduction organization has exactly one policy, which binds roles to members of the organization. These bindings are used to give these users permissions to invoke operations on this organization.
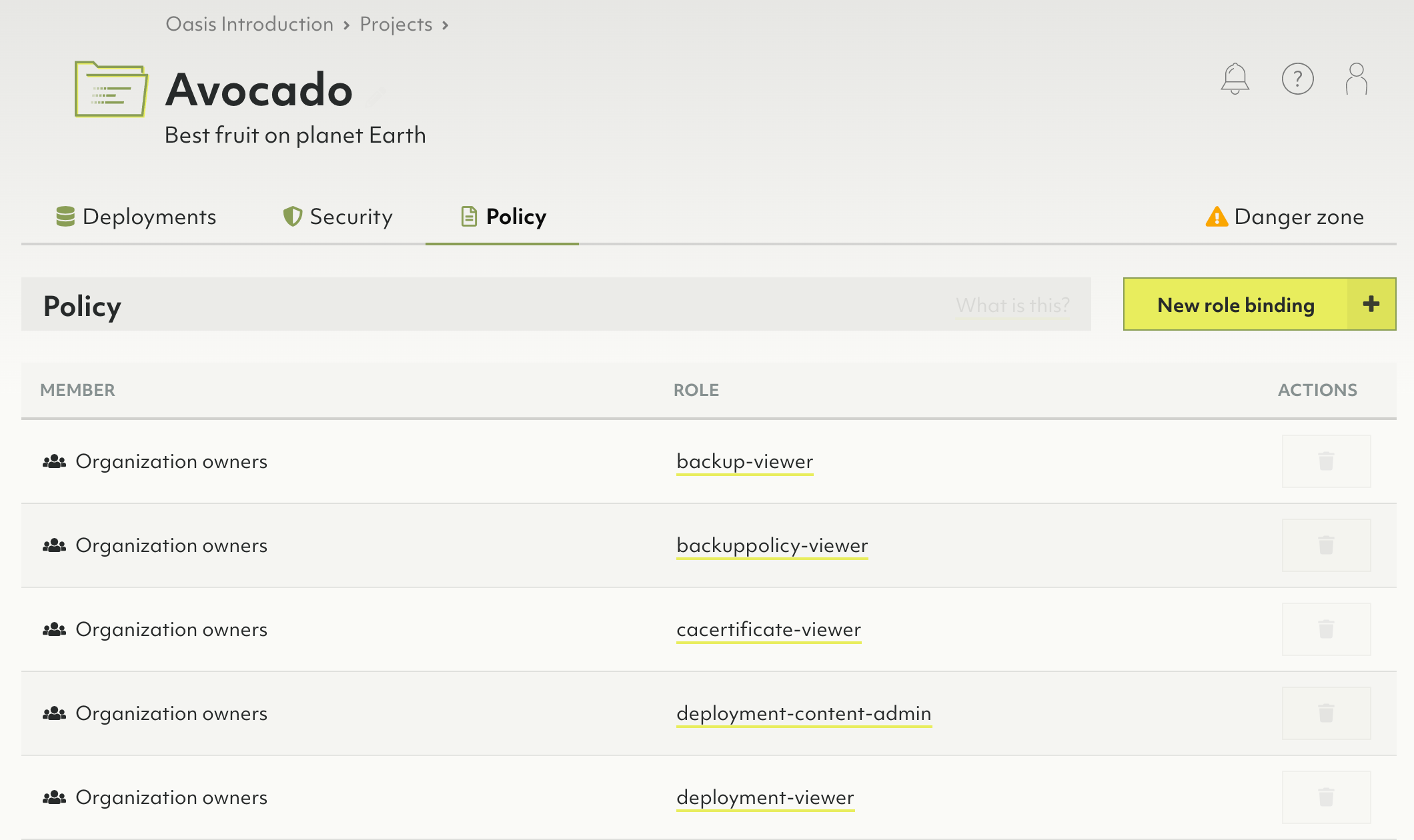
How to view, edit or remove role bindings of a policy
Decide whether you want to edit the policy of the organization or of a project or deployment and navigate the resource’s Policy tab.
- Organization: Click on Access Control in the main navigation, then click on the Policy tab.
- Project: Click on the desired project in the main navigation, then click on the Policy tab.
- Deployment: Click on the desired project in the main navigation, then on the title or view button of the desired deployment and finally click on the Policy tab.
To delete a role binding, click on the Trash bin icon in the Actions column.
Currently, you cannot edit a role binding, you can only delete it.
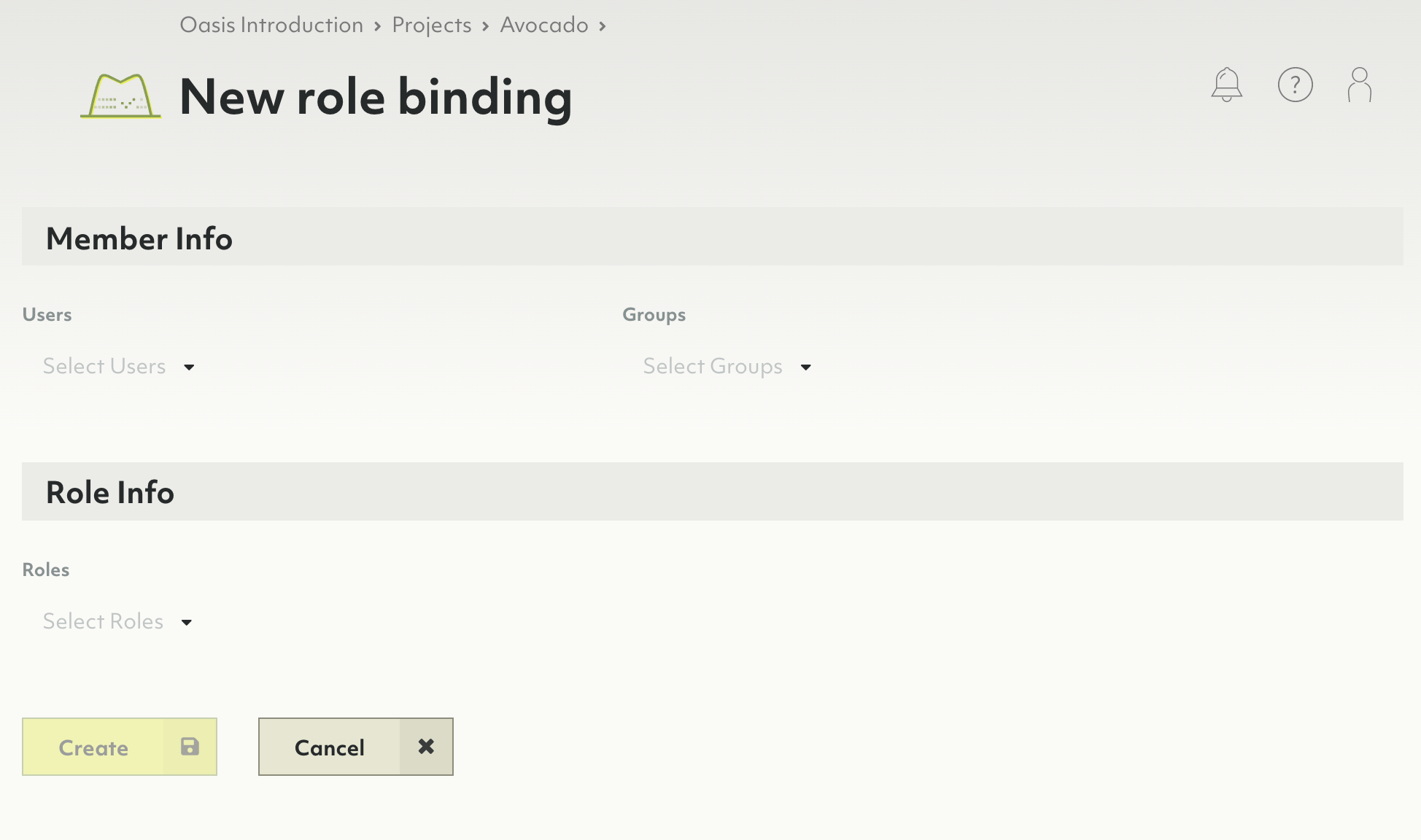
How to add a role binding to a policy
- Navigate to the Policy tab of an organization, project or deployment.
- Click on the New role binding button.
- Select one or more users and/or groups.
- Select the roles that you want to bind to the specified members.
- Click the Create button.
Roles
Operations on resources in Oasis require zero or more permissions. Since the number of permissions is large and very detailed, it is not practical to assign permissions directly to users. Instead Oasis has roles.
A role is a set of permissions. Roles can be bound to groups (preferably) or individual members. These bindings contribute to the respective organization, project or deployment policy.
There are predefined roles, but you can also create custom roles.
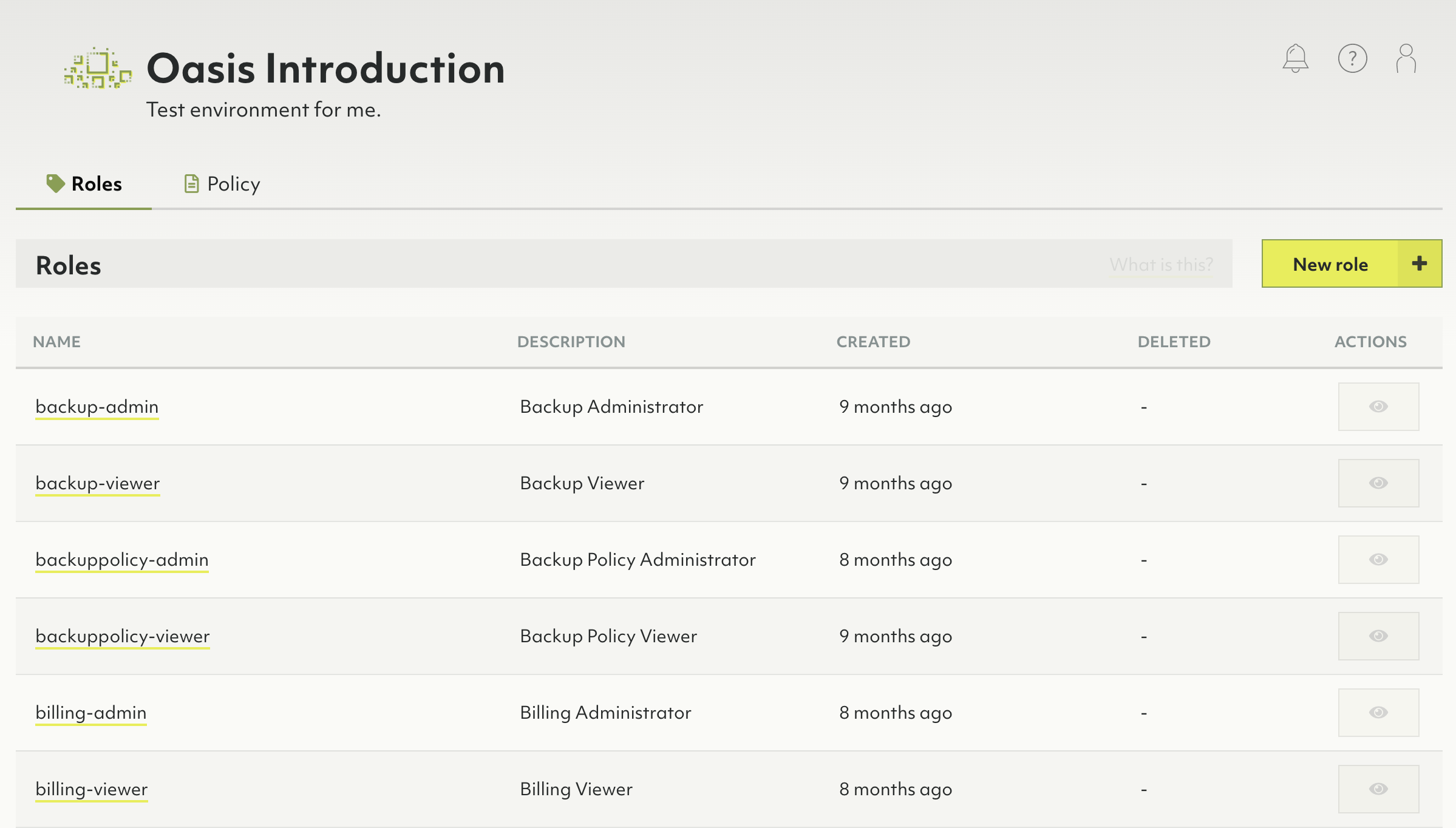
Predefined roles
Predefined roles are created by Oasis and group permissions together in a
logical role. An example of a predefine role is deployment-viewer. That role
contains all permissions needed to view deployments in a project.
Predefined roles cannot be deleted.
List of predefined roles and their permissions
Below roles are listed in this schema:
Description (ID):
Permission
Backup Administrator (backup-admin):
backup.backup.createbackup.backup.deletebackup.backup.listbackup.backup.getbackup.backup.updatebackup.backup.downloadbackup.backup.restoredata.deployment.restore-backup
Backup Viewer (backup-viewer):
backup.feature.getbackup.backup.getbackup.backup.list
Backup Policy Administrator (backuppolicy-admin):
backup.backuppolicy.createbackup.backuppolicy.deletebackup.backuppolicy.listbackup.backuppolicy.getbackup.backuppolicy.update
Backup Policy Viewer (backuppolicy-viewer):
backup.feature.getbackup.backuppolicy.getbackup.backuppolicy.list
Billing Administrator (billing-admin):
billing.config.getbilling.config.setbilling.invoice.getbilling.invoice.get-statisticsbilling.invoice.listbilling.organization.getbilling.paymentmethod.createbilling.paymentmethod.deletebilling.paymentmethod.getbilling.paymentmethod.get-defaultbilling.paymentmethod.listbilling.paymentmethod.set-defaultbilling.paymentmethod.updatebilling.paymentprovider.list
Billing Viewer (billing-viewer):
billing.config.getbilling.invoice.getbilling.invoice.get-statisticsbilling.invoice.listbilling.organization.getbilling.paymentmethod.getbilling.paymentmethod.get-defaultbilling.paymentmethod.listbilling.paymentprovider.list
CA Certificate Administrator (cacertificate-admin):
crypto.cacertificate.createcrypto.cacertificate.deletecrypto.cacertificate.listcrypto.cacertificate.getcrypto.cacertificate.set-defaultcrypto.cacertificate.update
CA Certificate Viewer (cacertificate-viewer):
crypto.cacertificate.getcrypto.cacertificate.list
Deployment Administrator (deployment-admin):
data.cpusize.listdata.deployment.createdata.deployment.create-test-databasedata.deployment.deletedata.deployment.resumedata.deployment.getdata.deployment.listdata.deployment.updatedata.deploymentfeatures.getdata.deploymentprice.calculatedata.limits.getdata.nodesize.listdata.presets.listmonitoring.logs.get
Deployment Content Administrator (deployment-content-admin):
data.cpusize.listdata.deployment.create-test-databasedata.deployment.getdata.deployment.listdata.deploymentcredentials.getdata.deploymentfeatures.getdata.limits.getdata.nodesize.listdata.presets.listmonitoring.logs.get
Deployment Viewer (deployment-viewer):
data.cpusize.listdata.deployment.getdata.deployment.listdata.deploymentfeatures.getdata.limits.getdata.nodesize.listdata.presets.list
Example Datasets Viewer (exampledataset-viewer):
example.exampledataset.listexample.exampledataset.get
Example Dataset Installation Administrator (exampledatasetinstallation-admin):
example.exampledatasetinstallation.listexample.exampledatasetinstallation.getexample.exampledatasetinstallation.createexample.exampledatasetinstallation.updateexample.exampledatasetinstallation.delete
Example Dataset Installation Viewer (exampledatasetinstallation-viewer):
example.exampledatasetinstallation.listexample.exampledatasetinstallation.get
Group Administrator (group-admin):
iam.group.createiam.group.deleteiam.group.listiam.group.getiam.group.update
Group Viewer (group-viewer):
iam.group.getiam.group.list
IAM provider Administrator (iamprovider-admin):
security.iamprovider.createsecurity.iamprovider.deletesecurity.iamprovider.getsecurity.iamprovider.listsecurity.iamprovider.set-defaultsecurity.iamprovider.update
IAM provider Viewer (iamprovider-viewer):
security.iamprovider.getsecurity.iamprovider.list
IP allowlist Administrator (ipallowlist-admin):
security.ipallowlist.createsecurity.ipallowlist.deletesecurity.ipallowlist.getsecurity.ipallowlist.listsecurity.ipallowlist.updatesecurity.ipallowlist.createsecurity.ipallowlist.deletesecurity.ipallowlist.getsecurity.ipallowlist.listsecurity.ipallowlist.update
IP allowlist Viewer (ipallowlist-viewer):
security.ipallowlist.getsecurity.ipallowlist.listsecurity.ipallowlist.getsecurity.ipallowlist.list
Organization Administrator (organization-admin):
billing.organization.getresourcemanager.organization.deleteresourcemanager.organization.getresourcemanager.organization.updateresourcemanager.organization-invite.createresourcemanager.organization-invite.deleteresourcemanager.organization-invite.getresourcemanager.organization-invite.listresourcemanager.organization-invite.update
Organization Viewer (organization-viewer):
billing.organization.getresourcemanager.organization.getresourcemanager.organization-invite.getresourcemanager.organization-invite.list
Policy Administrator (policy-admin):
iam.policy.getiam.policy.update
Policy Viewer (policy-viewer):
iam.policy.get
Project Administrator (project-admin):
resourcemanager.project.createresourcemanager.project.deleteresourcemanager.project.getresourcemanager.project.listresourcemanager.project.update
Project Viewer (project-viewer):
resourcemanager.project.getresourcemanager.project.list
Replication Administrator (replication-admin):
replication.deployment.clone-from-backup
Role Administrator (role-admin):
iam.role.createiam.role.deleteiam.role.listiam.role.getiam.role.update
Role Viewer (role-viewer):
iam.role.getiam.role.list
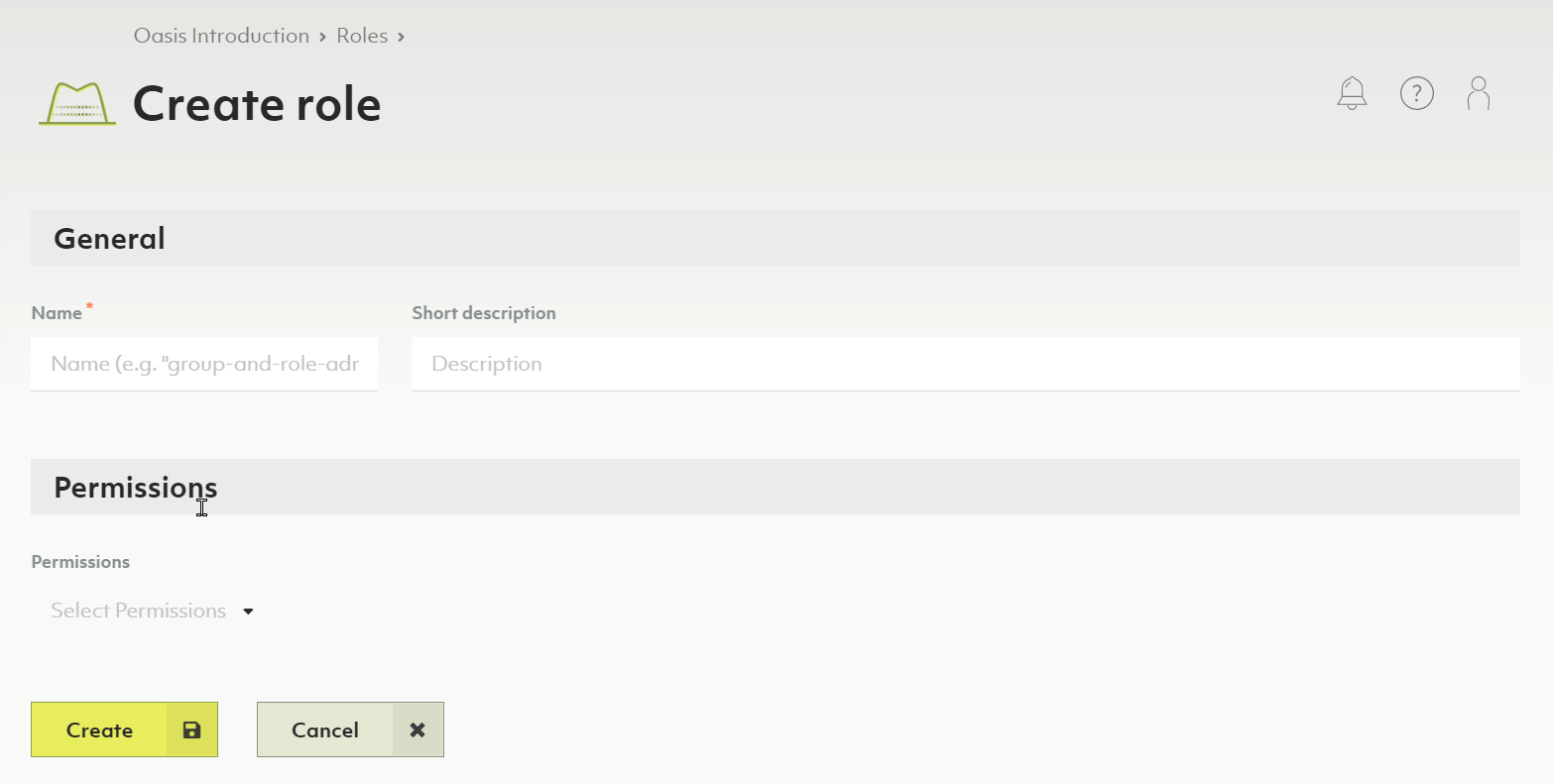
How to create a custom role
- Click on Access Control in the main navigation.
- On the Roles tab, click on the New role button.
- Enter a name and optionally a description for the new role.
- Select the desired permissions.
- Click the Create button.
How to view, edit or remove a custom role
- Click on Access Control in the main navigation.
- On the Roles tab, click on:
- A role name or the eye icon in the Actions column to view the role.
- The pencil icon in the Actions column to edit the role. You can also view a role and click the Edit button in the detail view.
- The trash can icon to delete the role. You can also view a role and click the Delete button in the detail view.
Permissions
Each operation (invoked on a resource) requires zero or more permissions.
A permission is a constant string such as resourcemanager.project.create,
following the schema <api>.<kind>.<verb>.
Permissions are solely defined by the Oasis API.
| API | Kind | Verbs |
|---|---|---|
backup |
backuppolicy |
create, delete, get, list, update |
backup |
backup |
create, delete, download, get, list, restore, update |
backup |
feature |
get |
billing |
config |
get, set |
billing |
invoice |
get, get-statistics, list |
billing |
organization |
get |
billing |
paymentmethod |
create, delete, get, get-default, list, set-default, update |
billing |
paymentprovider |
list |
crypto |
cacertificate |
create, delete, get, list, set-default, update |
data |
cpusize |
list |
data |
deploymentcredentials |
get |
data |
deploymentfeatures |
get |
data |
deploymentprice |
calculate |
data |
deployment |
create, create-test-database, delete, get, list, restore-backup, resume, update |
data |
limits |
get |
data |
nodesize |
list |
data |
presets |
list |
example |
exampledatasetinstallation |
create, delete, get, list, update |
example |
exampledataset |
get, list |
iam |
group |
create, delete, get, list, update |
iam |
policy |
get, update |
iam |
role |
create, delete, get, list, update |
monitoring |
logs |
get |
replication |
deployment |
clone-from-backup |
resourcemanager |
organization-invite |
create, delete, get, list, update |
resourcemanager |
organization |
delete, get, update |
resourcemanager |
project |
create, delete, get, list, update |
security |
iamprovider |
create, delete, get, list, set-default, update |
security |
ipallowlist |
create, delete, get, list, update |
Permission inheritance
Each resource has its own policy, but this does not mean that you have to repeat access control bindings on all these policies.
Once you assign a role to a user (or group of users) in a policy at one level, all the permissions of that role are inherited in lower levels. That is, permissions are inherited downwards from an organization to its projects and from a project to its deployments.
For more inclusive permissions, add the highest permission for a member or
group at the at the organization level.
For example, if you bind the role deployment-viewer to user John in the
policy of an organization, John will have all the permissions contained in
that role in all projects of that organization and all deployments in those
projects as well.
For more restrictive permissions, add the highest permission at the project
or even deployment level, and least permission at the organization level.
For example, if you bind the role deployment-viewer to user John
in a project, John will have all the permissions contained in that role in
that project as well as in all deployments contained in that project, but not
in other projects of the containing organization.
Inheritance example
- Imagine you have a group Deployers.
- That group holds all persons that deal with deployments.
- Further imagine you have a role Deployment Viewer, containing permission
data.deployment.getanddata.deployment.list. - You could now add a role binding of Deployers to Deployment Viewer.
- If you add the binding to the organization policy, the members of this group will be granted the defined permissions for the organization, all its projects and all its deployments.
- If you add it project A’s policy, the members of this group will be granted the defined permissions for project A only and its deployments, but not for other projects and its deployments.
- If you add it to deployment X’s policy of project A, the members of this group will be granted the defined permissions for deployment X only, and not any other deployment of project A or any other project of the organization.
The role Deployment viewer is effective on the following entities depending on which policy the binding is added to:
| Role binding added to → Role effective on ↓ |
Organization policy | Project A’s policy | Deployment X’s policy of project A |
|---|---|---|---|
| Organization, its projects and deployments | ✓ | — | — |
| Project A and its deployments | ✓ | ✓ | — |
| Project B and its deployments | ✓ | — | — |
| Deployment X of project A | ✓ | ✓ | ✓ |
| Deployment Y of project A | ✓ | ✓ | — |
| Deployment Z of project B | ✓ | — | — |

